Example 16: Security
Overview
In this example we cover various aspects of security both static code checks that are automatic done during build and techniques used to dynamically secure the UI. Dynamic security testing is not covered here but the extension framework does support it.
You can find the code for the example in our GitHub repository.
Important: Wincom offers these services but cannot be held responsible for the effectiveness of otherwise of the security provided by this code.
Implementation
Reporting
There are three reports generated during build
- Security - Results of static analysis tools, data in this report should be used to assist in creating the Test Plan
- Test Plan - Generated from a Java file that contains the functional and security testing
- Audit - Used to determine the size and scope of the application
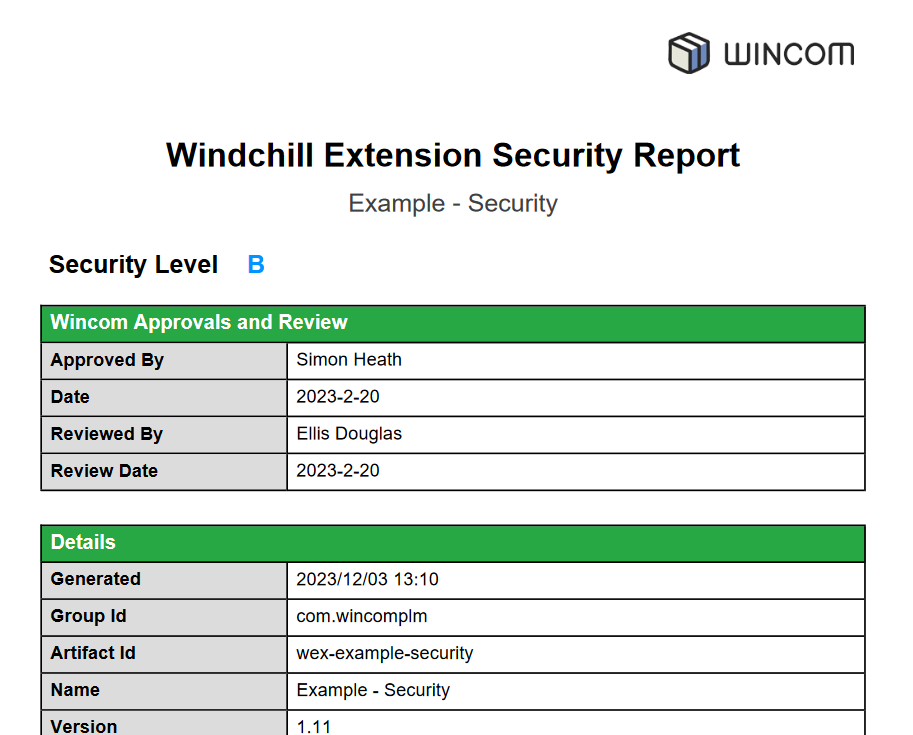
Security Report
On every build a test report will be generated
The report will also be appended with any other PDF documentation that is in the extension security area
 iate
iate
The security report contains the following sections:
- Security Level - A-D this is set manually in the meta.json but must be equal or higher that the automatic suggestion
- Approvals and Reviews - Dates and users that approved
- Details - Extension details
- Security - A list of checks that were enabled during the build
- CVE Suppresions - A list of suppressions (if any) that were applied
- Security Information - The security levels
- End Points - Any URL access points, that might require testing
- Build Configuration - Version of all tools used to build the report
- Legal Notice
- All additional PDF information is appended to the report
Securing for XSS Vulnerabilities
Coding
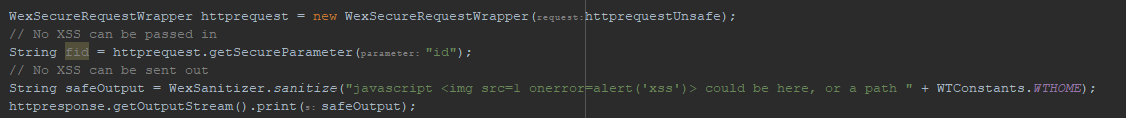
An XSS vulnerability is a common issue that needs to be protected against
This example use the library wt-security-commons that in turn uses com.googlecode.owasp-java-html-sanitizer
Securing a UI Page
Security is in most cases not required for the UI, as Windchill itself manages security and access control to data. However, if we do wish to allow access only to a certain group of users e.g admins, we can use the WEX Framework's wt-security-commons code to do this:
import com.wincomplm.wex.security.commons.impl.WexSecurePage;
@WexMethod(name = "securePage", description = "A simple security example")
public void securePage() throws Exception {
if (!WexAdminCheckAccess.instance.isSiteOrBusinessAdmin()) {
httpresponse.sendError(403, "User is not an administrator.");
}
}//securePage
Also, try to access the URL directly as a non-admin user:
http://{your_host}/Windchill/ptc1/com/wincomplm/wex/example/ui/edkHelloWorld
You will get the error below:
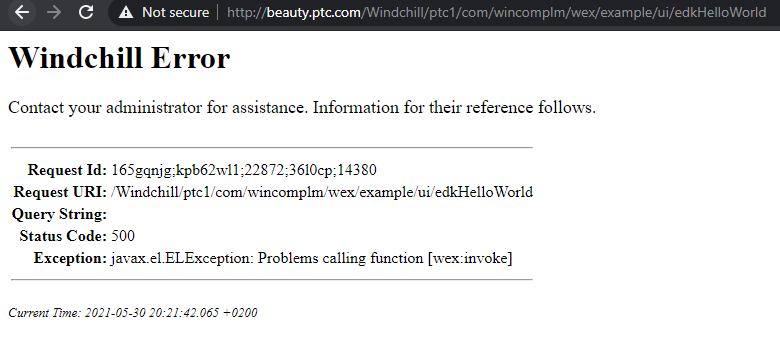
This error gives little information, which is intentional as security-related errors should disclose as little information as possible. However, the MS logs clearly show the cause:
wt.util.WTException: User must be site administrator to access page
...
com.wincomplm.wex.example.ui.impl.ui.methods.ExampleUIMethods.securePage(ExampleUIMethods.java:24)
Rate limiting
On certain operations it is important to rate limit to avoid an exhausting of resources e.g. disk space
This can be coded using the limiter
static WexPerUserRateLimiter limiter = WexPerUserRateLimiter.newPerUserRateLimiter(10, TimeUnit.MILLISECONDS.convert(10, TimeUnit.MINUTES));
@WexMethod(name = "get-example-data", description = "Get example")
public void getExampleData(HttpServletRequest httprequestUnsafe, HttpServletResponse httpresponse) throws Exception {
limiter.checkException();
}//getExampleData
Security Approval and Exclusions
The extension can implement the following in the security area
- owasp-suppress.xml - Used to suppress any CVE issues
- sca-approvals - Used to allow libraries to be included in the extension
- wve-approvals - Approval of WVE warnings
UI and JUnit implementation
The user guide give access to the following pages
Which is an admin only page and will be rejected for other users.
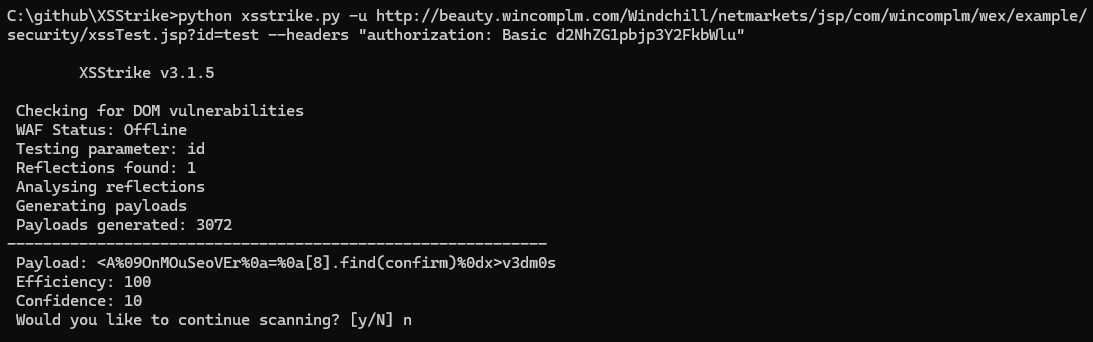
XSS Test Page
This test will provoke an XSS as the payload will be executed
To ensure the page is not vulnerable to XSS
python xsstrike.py -u http://beauty.wincomplm.com/Windchill/netmarkets/jsp/com/wincomplm/wex/example/security/xssTest.jsp?id=test --headers "authorization: Basic d2NhZG1pbjp3Y2FkbWlu"
an automated tool should be used, such as XSStrike
Runs all the Junit tests